A Network Utilizes a Network Access Control
It also monitors and controls their activity once they are on the network. The controlled access method is deterministic not a contention-based access to networks.
When a wired or wireless host tries to connect to the network a NAC agent on the host checks it to make sure it has all of the latest operating system updates installed and that the latest antivirus definitions have been applied.

. A network utilizes a network access control NAC solution to protect against malware. By using this model network administrators can more effectively manage activity and access based on individual requirements. Identity-Based Access Control IBAC.
Wired Ethernet networks use CSMACD for media access control. When a wired or wireless host tries to connect to the network a NAC agent on the host checks it to make sure it has all of the latest operating system updates installed and that the latest antivirus definitions have been applied. Network Access Control or NAC as its commonly referred to is a process by which before network access is given a user or a device.
Its better at preventing network attacks. The market growth is. Media access control defines the way data frames get placed on the media.
Media access control defines the way data frames get placed on the media. Wired Ethernet networks use CSMACD for media access control. Wired Ethernet networks use CSMACD for media access control.
A network utilizes a network access control NAC solution to protect against malware. Network access control is also known as network admission control NAC. The controlled access method is deterministic not a.
All clients on the network are equal in terms of providing and using resources and each individual workstation authenticates its users. The Data Link Layer utilizes what name for its protocol data unit PDU. Rogue DHCP server B.
IEEE 80211 wireless networks use CSMACA a similar method. 18 hours agoThe network access control NAC market size is expected to record a valuation of USD 20 billion by 2028 according to the most recent study by Global Market Insights Inc. What is this process called.
A control model in which access rights are regulated by a central authority based on multiple levels of security. It works better on external networks. A network utilizes a network access control NAC solution to protect against malware.
A typical network access control scheme comprises of two major components such as Restricted Access and Network Boundary Protection. IEEE 80211 wireless networks use CSMACA a similar method. A router can only send data to another computer thats on the same network.
Restricted Access to the network devices is achieved through user authentication and authorization control which is responsible for identifying and authenticating different users to the network system. Flow control congestion control - Restricts the amount of data the sender can send to a receiver. It utilizes less memory.
Network access control is a significant component in the effort of providing the end-users and devices accessing your network with everything they need nothing more and nothing less. A _______ network is a network in which resource sharing processing and communications control are completely decentralized. Networks with controlled access have reduced performance due to data collisions.
Share this link with a friend. Explain connection services at layer 3. A router is a set of components that makes up computer networking.
Makes communication more reliable when connection services at layer 2 is not operating. The controlled access method is deterministic not a contention-based access to networks. Network access controls implement a defined security policy for access which is supported by a network access server that.
Next Steps Its great to offer wireless access to your employees guests and customers however its not as simple as buying some routers and turning them on. Security Enhanced Linux is implemented using MAC on. Network Layer Layer 3.
A router connects lots of. It is a network solution that enables only compliant authenticated and trusted endpoint devices and nodes to access network resources and infrastructure. With the information from the IAM along with a pre-established list of rules set by the business using.
Network access control is the process of restricting the access to network resources by devices that are used by the end user. What is not a variable that a network access control list can filter traffic with. Explain the functions provided by connection services at layer 3.
A technician is setting up a direct connection between two older PCs so they can communicate but not be on the corporate networkThe technician does not have access to a spare switch but does have spare Cat 6 cables RJ-45 plugs and a crimping toolThe technician cuts off one end of the cable. The default admin username is still in use. A network administrator needs to filter unwanted packets when implementing the companys.
After being routed the efforts at connection the network access control system confirms privileges using an identity and access management IAM a program that checks users for appropriate permissions to access data materials as indicated by internal policies. Checks it to make sure it has all of the latest operating system updates installed and thatt. A conventional network access server NAS can carry out functions like authentication and.
Network access control NAC refers to a method that helps in boosting the safety of a patented network by limiting the availability of network resources to endpoint protection devices that follow a defined security policy. The default admin password is still in use. Match the port security MAC address type on the left with its description on the.
Mandatory Access Control MAC. A router utilizes network protocols to help determine where to send data packets. Media access control defines the way data frames get placed on the media.
IEEE 80211 wireless networks use CSMACA a similar method.

Pin By Quentin Bob On Data Com Networking Basics Network Performance Erp System
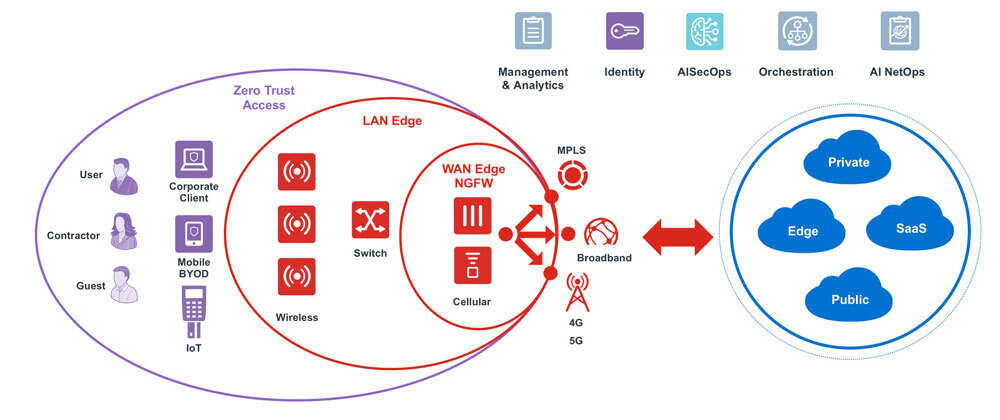
Premier Network Access Control Nac Solutions Security Fortinet

Access Control Security Systems Cloud Computing Access Control Active Directory
Comments
Post a Comment